We Need White Hat Hackers
Introduction:
White hat hackers – sometimes also called “ethical hackers” or “good hackers” – are the antithesis of black hats. They exploit computer systems or networks to identify their security flaws so they can make recommendations for improvement.
Is white hat hacker a job?
Image result for white is white hat hacker
A White Hat Hacker plays a key role in cyber security. As ethical hackers they thwart attacks in real time. Certified Ethical Hackers work in health care, finance, government, energy and much more. So, if you want to put programming skills to use, this may be a perfect career path.
Who is a famous white hat hacker?
Dan Kaminsky: Dan Kaminsky has played a large role in fighting cybercrime since 2008, when he became one of the most widely known white hat hackers
What do hackers study in college?
There are several education requirements to become a Hacker. Hackers usually study Computer Science, Computer Engineering or Finance. 44% of Hackers hold a Bachelor's Degree and 28% hold a High School Diploma.
Who is the No 1 hacker in the world?
Image result
Kevin Mitnick
Is the world's authority on hacking, social engineering, and security awareness training. In fact, the world's most used computer-based end-user security awareness training suite bears his name.
What Is a White Hat Hacker?
A White Hat hacker tests systems and networks by trying to break into them. They are hackers, but their talents are being used to improve Cyber Security. Being hackers, they are familiar with the tactics that malicious hackers use to compromise systems; White Hat hackers try to find the vulnerabilities before the bad guys do.
The most significant difference between Black Hat and White Hat hackers is that the latter is permitted by companies to try and break into their Cyber Security systems.
White Hat hackers are also called “Ethical Hackers” or “Certified Ethical Hackers.” In some instances, White Hat hackers assume other Cyber Security titles within an organization.
- Cybersecurity analyst
- Information security analyst
- Intrusion detection analyst
- IT security engineer
- IT security administrator
- Network security analyst
- Penetration tester
Note that sometimes a White Hat hacker also ends up becoming responsible for not just the digital aspect of Cyber Security but for the hardware end of it was well. This responsibility potentially means that you would also be responsible for the integrity of hardware like keypad controls and badge readers. You may even need to educate fellow employees on Cyber Security tips relating to the handling, transportation, and storage of their devices such as laptops, phones, and pads.
Why Do We Need White Hat Hackers?
According to Statista, there were 3.9 billion Internet users in 2018 and 4.3 billion Internet users so far this year. As impressive as that sounds, it’s eclipsed by predictions that the number of people online will triple from 2015 to 2022, hitting six billion users. As a result, these figures tell us that 90% of Earth’s population, aged six and older, will be online by 2030.
Furthermore, retail e-commerce sales hit $2.3 trillion and is projected to top $4.88 trillion by 2021. Also, projections indicate that mobile devices will be used to conduct almost three-fourths of all e-commerce transactions.
The statistics offer substantial evidence of our world’s continually escalating reliance on the Internet. Consequently, this rise in online use provides a rich field of opportunities for cyber-criminals to perpetrate everything from minor privacy violations to outright larceny and fraud.
The problem is already out there in a big way. Financial losses from cybercrime are expected to reach $6 trillion every year by 2021, a two-fold increase from 2015. At the same time, predictions further state that the number of unfilled cybersecurity jobs will top 3.5 million by 2021, a significant boost over the one million vacant positions in 2014.
These sobering figures illustrate why there’s such a desperate need for White Hat hackers. More users mean more mobile usage, more networks, and more websites. E of these elements needs to be tested thoroughly, run through their paces to make sure that cyber-criminal hackers can’t penetrate their defenses. More testers are required to address this shortage.
By taking all of these elements and putting them together into one picture, we see a vast field of potential for up and coming Cyber Security professionals. IT professionals who are looking for a secure domain with a lot of possibilities for growth need to look into White Hat hackers jobs.
Even if you’re already working in an IT department and have no intention of running off to become an ethical hacker, it’s to your advantage to learn the tricks of the hackers’ trade. It’s always a smart idea to upskill whenever you have the opportunity, as it adds to your skill base and makes you a more valuable asset. Besides, if you do plan on moving on to green pastures at some point, it’s smart to bring a vast assortment of skills with you! It may be the crucial deciding factor in who gets that job!
This high demand is reflected in part by the kinds of salaries that a White Hat hacker can earn, as we’re about to see.
As the old saying goes, “It takes a thief to catch a thief.” In other words, the person most likely to successfully catch a thief is someone who knows the miscreant’s tactics, mindset, and habits. Cyber-related crime is the new frontier for larceny. This an increasingly ominous notion, considering how our information is collected, processed, and stored online. Add to that the boom in mobile computing, and you have quite a dilemma on your hands.
That’s why the best defense against Black Hat hackers is a group of white hat hackers who use their hacking talents for defensive purposes. In this article, we’ll cover everything you need to know about White Hat hackers, including how to become one, if you’re intrigued enough by the idea. Let us now begin with the White Hat Hacker definition.
What Is a White Hat Hacker?
A White Hat hacker tests systems and networks by trying to break into them. They are hackers, but their talents are being used to improve Cyber Security. Being hackers, they are familiar with the tactics that malicious hackers use to compromise systems; White Hat hackers try to find the vulnerabilities before the bad guys do.
The most significant difference between Black Hat and White Hat hackers is that the latter is permitted by companies to try and break into their Cyber Security systems.
White Hat hackers are also called “Ethical Hackers” or “Certified Ethical Hackers.” In some instances, White Hat hackers assume other Cyber Security titles within an organization.
- Cybersecurity analyst
- Information security analyst
- Intrusion detection analyst
- IT security engineer
- IT security administrator
- Network security analyst
- Penetration tester
Note that sometimes a White Hat hacker also ends up becoming responsible for not just the digital aspect of Cyber Security but for the hardware end of it was well. This responsibility potentially means that you would also be responsible for the integrity of hardware like keypad controls and badge readers. You may even need to educate fellow employees on Cyber Security tips relating to the handling, transportation, and storage of their devices such as laptops, phones, and pads.
Why Do We Need White Hat Hackers?
According to Statista, there were 3.9 billion Internet users in 2018 and 4.3 billion Internet users so far this year. As impressive as that sounds, it’s eclipsed by predictions that the number of people online will triple from 2015 to 2022, hitting six billion users. As a result, these figures tell us that 90% of Earth’s population, aged six and older, will be online by 2030.
Furthermore, retail e-commerce sales hit $2.3 trillion and is projected to top $4.88 trillion by 2021. Also, projections indicate that mobile devices will be used to conduct almost three-fourths of all e-commerce transactions.
The statistics offer substantial evidence of our world’s continually escalating reliance on the Internet. Consequently, this rise in online use provides a rich field of opportunities for cyber-criminals to perpetrate everything from minor privacy violations to outright larceny and fraud.
The problem is already out there in a big way. Financial losses from cybercrime are expected to reach $6 trillion every year by 2021, a two-fold increase from 2015. At the same time, predictions further state that the number of unfilled cybersecurity jobs will top 3.5 million by 2021, a significant boost over the one million vacant positions in 2014.
These sobering figures illustrate why there’s such a desperate need for White Hat hackers. More users mean more mobile usage, more networks, and more websites. E of these elements needs to be tested thoroughly, run through their paces to make sure that cyber-criminal hackers can’t penetrate their defenses. More testers are required to address this shortage.
By taking all of these elements and putting them together into one picture, we see a vast field of potential for up and coming Cyber Security professionals. IT professionals who are looking for a secure domain with a lot of possibilities for growth need to look into White Hat hackers jobs.
Even if you’re already working in an IT department and have no intention of running off to become an ethical hacker, it’s to your advantage to learn the tricks of the hackers’ trade. It’s always a smart idea to upskill whenever you have the opportunity, as it adds to your skill base and makes you a more valuable asset. Besides, if you do plan on moving on to green pastures at some point, it’s smart to bring a vast assortment of skills with you! It may be the crucial deciding factor in who gets that job!
This high demand is reflected in part by the kinds of salaries that a White Hat hacker can earn, as we’re about to see.
How Much Do White Hat Hackers Make?
aOne of the nifty things about being a White Hat hacker is that you get to tackle the challenge of breaking into a company’s system, and get paid to do it! How much pay, you ask? According to payscale, a certified ethical hacker earns an annual average of $90,000.
A White Hat hacker’s salary in India comes in at Rs 476,017 annually, whereas in Canada a CEH in similar circumstances can earn C$68,000. Australian White Hat hackers earn an annual average of AU$100K. Furthermore, White Hat hackers in the United Kingdom and South Africa can make a yearly average of £36,595 and R479,000, respectively.
If you want to earn a higher salary, it’s a good idea to specialize. However, it’s essential you have a good grasp of the overall concepts and practices of White Hat hacking first.
How Much Do White Hat Hackers Make?
aOne of the nifty things about being a White Hat hacker is that you get to tackle the challenge of breaking into a company’s system, and get paid to do it! How much pay, you ask? According to payscale, a certified ethical hacker earns an annual average of $90,000.
A White Hat hacker’s salary in India comes in at Rs 476,017 annually, whereas in Canada a CEH in similar circumstances can earn C$68,000. Australian White Hat hackers earn an annual average of AU$100K. Furthermore, White Hat hackers in the United Kingdom and South Africa can make a yearly average of £36,595 and R479,000, respectively.
If you want to earn a higher salary, it’s a good idea to specialize. However, it’s essential you have a good grasp of the overall concepts and practices of White Hat hacking first.
How Can You Become a Certified White Hat Hacker?
If everything you’ve read so far as caught your interest, then you need to figure out how one goes about becoming a White Hat hacker. For starters, it’s essential to have some education in the field. It’s especially useful to have a bachelor’s or master’s degree in a relevant area such as computer programming, computer science, information security, or information technology.
Keep in mind that not all companies have the same educational requirements. Some businesses will accept actual hands-on experience in place of a degree, provided it’s at least a couple of years, and it’s in an appropriate field. Don’t expect three years in the mailroom to be your ticket to White Hat hacking. If, on the other hand, you’ve spent a few years doing IT-related jobs, then you’re in good shape.
Next, you need specialized White Hat hacker training and White Hat hacker certification. Certification is crucial because it tells a prospective employer that you are proficient in the necessary skills and techniques needed to carry out your responsibilities. Fortunately, there are many resources out there to choose from.
In addition to Ethical hacking certification, which is also referred to as the White Hat hacking course in some circles, there are several additional security certifications that you should earn. In the fast-paced, competitive world of Cyber Security, the more you know, the better! The certifications include:
- Certified Information Systems Security Professional (CISSP)
- Certified Information Systems Auditor (CISA)
- Certified Information Security Manager (CISM)
- Certified Cloud Security Professional (CCSP)
- Licensed Penetration Tester (LPT) Master
Finally, if you haven’t already gained some on-the-job experience, you should do so. Nothing teaches as well as doing the task itself and learning from it. With all of these elements in place, you will be ready to strike out on your own as a capable White Hat hacker!
Presenting an Effective Method of Learning
If all of the certifications mentioned above seem intimidating, then relax, your worries are over. Fortunately, Simplilearn offers you a one-stop shopping experience where you can gain all of the necessary training and certifications you need to achieve your White Hat hacker goal!
For starters, there’s the CEH (v10) Certified Hacking Course. This course will train you on the advanced step-by-step methodologies that hackers use, including writing virus codes and reverse engineering, so you can better protect corporate infrastructure from data breaches. The course also helps you master advanced network packet analysis and advanced system penetration testing techniques, enabling you to build your network security skill-set and beat hackers at their own game. The course is available as either a corporate training solution or an online classroom Flexi-Pass for individuals.
Simplilearn also offers training courses in many of the Cyber Security assets mentioned earlier.
The Certified Information Systems Security Professional (CISSP) certification is considered the gold standard in the domain of information security. This training is aligned with (ISC)² CBK 2018 requirements and will train you to become an information assurance professional who defines all aspects of IT security, including architecture, design, management, and controls. Most IT security positions require or prefer a CISSP certification, so this one’s crucial.
The Certified Information Systems Auditor (CISA) certification cour is aligned with the latest 2019 edition of the CISA exam. It'll provide you the skillsets to govern and manage enterprise IT and perform an effective security audit on any organization. You will gain expertise in the acquisition, development, testing, and implementation of information systems and learn the guidelines, standards, and best practices for protecting them.
The Certified Information Security Manager (CISM) course is an essential certification for information security professionals who want to assess, design, manage, and oversee enterprise information security. This CISM course is closely aligned with ISACA's best practices and teaches you how to define and design enterprise security architecture. You will also learn how to achieve IT compliance and governance while delivering reliable service to customers. Furthermore, the course teaches you how IT security systems can be used to achieve business goals and objectives. The Certified Cloud Security Professional (CCSP) training course is the leading certification by (ISC)² and will teach you to negate security threats to your cloud storage by understanding information security risks and strategies to maintain data security. Covering the six sections of the Official (ISC)² CCSP Common Body of Knowledge (CBK®), this course will help you pass the exam obtaining your CCSP.
Follow the training paths, take the courses, and master the top strategies and tactics of White Hat hackers, so that you can be ready to launch into an exciting and rewarding new career!
First we study some intresting thing's
The first lesson of cyber security:
The Scale of the Cyber Security Threat
According to Forbes, 2022 will present us with a pack of diverse and terrifying cyber security challenges, everything from supply chain disruption to increased smart device risks to a continued cyber security talent drought.
According to Cybercrime Magazine, cybercrime will cost the world $10.5 trillion annually by 2025! Furthermore, global cybercrime costs are predicted to rise by almost 15 percent yearly over the next four years.
Concepts such as the pandemic, cryptocurrency, and the rise in remote working are coming together to create a target-rich environment for criminals to take advantage of.
What is Cyber Security?
Cyber security is a discipline that covers how to defend devices and services from electronic attacks by nefarious actors such as hackers, spammers, and cybercriminals. While some components of cyber security are designed to strike first, most of today's professionals focus more on determining the best way to defend all assets, from computers and smartphones to networks and databases, from attacks.
Cyber security has been used as a catch-all term in the media to describe the process of protection against every form of cybercrime, from identity theft to international digital weapons. These labels are valid, but they fail to capture the true nature of cyber security for those without a computer science degree or experience in the digital industry.
Cisco Systems, the tech conglomerate specializing in networking, the cloud, and security, defines cyber security as “…the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes.”
How Does Cyber Security Work? The Challenges of Cyber Security
Cyber security encompasses technologies, processes, and methods to defend computer systems, data, and networks from attacks. To best answer the question “what is cyber security” and how cyber security works, we must divide it into a series of subdomains:
Application Security
Application security covers the implementation of different defenses in an organization’s software and services against a diverse range of threats. This sub-domain requires cyber security experts to write secure code, design secure application architectures, implement robust data input validation, and more, to minimize the chance of unauthorized access or modification of application resources.
Cloud Security
Cloud security relates to creating secure cloud architectures and applications for companies that use cloud service providers like Amazon Web Services, Google, Azure, Rackspace, etc.
Identity Management and Data Security
This subdomain covers activities, frameworks, and processes that enable authorization and authentication of legitimate individuals to an organization’s information systems. These measures involve implementing powerful information storage mechanisms that secure the data, whether in transition or residing on a server or computer. In addition, this sub-domain makes greater use of authentication protocols, whether two-factor or multi-factor.
Mobile Security
Mobile security is a big deal today as more people rely on mobile devices. This subdomain protects organizational and personal information stored on mobile devices like tablets, cell phones, and laptops from different threats like unauthorized access, device loss or theft, malware, viruses, etc. In addition, mobile security employs authentication and education to help amplify security.
Network Security
Network security covers hardware and software mechanisms that protect the network and infrastructure from disruptions, unauthorized access, and other abuses. Effective network security protects organizational assets against a wide range of threats from within or outside the organization.
Disaster Recovery and Business Continuity Planning
Not all threats are human-based. The DR BC subdomain covers processes, alerts, monitoring, and plans designed to help organizations prepare for keeping their business-critical systems running during and after any sort of incident (massive power outages, fires, natural disasters), and resuming and recovering lost operations and systems in the incident’s aftermath.
User Education
Knowledge is power, and staff awareness of cyber threats is valuable in the cyber security puzzle. Giving business staff training on the fundamentals of computer security is critical in raising awareness about industry best practices, organizational procedures and policies, monitoring, and reporting suspicious, malicious activities. This subdomain covers cyber security-related classes, programs, and certifications.
What is Cyber Security and Types of Cyber Threats
Cybercrime is defined as any unauthorized activity involving a computer, device, or network. There are three generally recognized classifications of cybercrime: computer-assisted crimes, crimes where the computer itself is a target, and crimes where the computer is incidental to the crime rather than directly related.
Here is a list of common cyber threats:
- Cyberterrorism. This threat is a politically-based attack on computers and information technology to cause harm and create widespread social disruption.
- Malware. This threat encompasses ransomware, spyware, viruses, and worms. It can install harmful software, block access to your computer resources, disrupt the system, or covertly transmit information from your data storage.
- Trojans. Like the legendary Trojan Horse of mythology, this attack tricks users into thinking they're opening a harmless file. Instead, once the trojan is in place, it attacks the system, typically establishing a backdoor that allows access to cybercriminals.
- Botnets. This especially hideous attack involves large-scale cyberattacks conducted by remotely controlled malware-infected devices. Think of it as a string of computers under the control of one coordinating cybercriminal. What’s worse, compromised computers become part of the botnet system.
- Adware. This threat is a form of malware. It's often called advertisement-supported software. The adware virus is a potentially unwanted program (PUP) installed without your permission and automatically generates unwanted online advertisements.
- SQL injection. A Structured Query Language attack inserts malicious code into a SQL-using server.
- Phishing. Hackers use false communications, especially e-mail, to fool the recipient into opening it and following instructions that typically ask for personal information. Some phishing attacks also install malware.
- Man-in-the-middle attack. MITM attacks involve hackers inserting themselves into a two-person online transaction. Once in, the hackers can filter and steal desired data. MITM attacks often happen on unsecured public Wi-Fi networks.
- Man-in-the-middle attack. MITM attacks involve hackers inserting themselves into a two-person online transaction. Once in, the hackers can filter and steal desired data. MITM attacks often happen on unsecure public Wi-Fi networks.
- Denial of Service. DoS is a cyber attack that floods a network or computer with an overwhelming amount of “handshake” processes, effectively overloading the system and making it incapable of responding to user requests.
As data breaches, hacking, and cybercrime reach new heights, companies increasingly rely on cyber security experts to identify potential threats and protect valuable data. So it makes sense that the cyber security market is expected to grow from $217 billion in 2021 to $345 billion by 2026, posting a Compound Annual Growth Rate (CAGR) of 9.7% from 2021 to 2026.
The Advantages of Cyber Security
Today's cyber security industry is primarily focused on protecting devices and systems from attackers. While the bits and bytes behind these efforts can be hard to visualize, it's much easier to consider the effects. Without cyber security professionals working tirelessly, many websites would be nearly impossible to enjoy due to ever-present denial-of-service attack attempts. Imagine not having access to Simplilearn's community of experts and certified professionals — no more tips, tricks, and advice to help you achieve your professional goals!
Without solid cyber security defenses, it would be easy to destroy modern-day essentials like the power grids and water treatment facilities that keep the world running smoothly.
Simply put, cyber security is critically important because it helps to preserve the lifestyles we have come to know and enjoy.
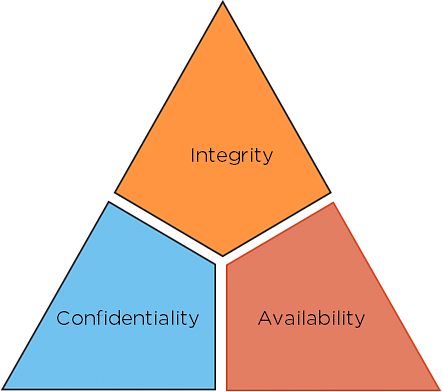
CIA Triad
The security of any organization starts with three principles: Confidentiality, Integrity, Availability. This is called as CIA, which has served as the industry standard for computer security since the time of first mainframes.
Fig: CIA triad
- Confidentiality: The principles of confidentiality assert that only authorized parties can access sensitive information and functions. Example: military secrets.
- Integrity: The principles of integrity assert that only authorized people and means can alter, add, or remove sensitive information and functions. Example: a user entering incorrect data into the database.
- Availability: The principles of availability assert that systems, functions, and data must be available on-demand according to agreed-upon parameters based on levels of service.
Who is a Cyber Security Expert?
As data breaches, hacking, and cybercrime reach new heights, companies are increasingly relying on Cyber Security experts to identify potential threats and protect valuable data. It makes sense that the Cyber Security market is expected to grow from $152 billion in 2018 to $248 billion by 2023.
So what do Cyber Security experts do? On any given day, they:
- Find, test, and repair weaknesses within a company's infrastructure.
- Monitor systems for malicious content
- Identify network breaches
- Install regular software updates, firewalls, and antivirus protection
- Strengthen areas where attacks may have occurred
They work in one or more of these common Cyber Security domains to keep data safe:
- Asset security: Analyze networks, computers, routers, and wireless access points
- Security architecture and engineering: Standardize security policies and procedures
- Communication and network security: Regulate cloud storage and data transfer
- Identity and access management: Track user authentication and accountability
- Security operations: Monitor security to identify attacks
- Security assessment and testing: Test security policies to ensure compliance with industry standards
- Software development security: Create and repeatedly test code
- Security and risk management: Identify potential risks and implement appropriate security controls
Cyber Security experts employ different tactics to secure computer systems and networks. Some of the best practices include:
- Using two-way authentication
- Securing passwords
- Installing regular updates
- Running antivirus software
- Using firewalls to disable unwanted services
- Avoiding phishing scams
- Employing cryptography, or encryption
- Securing domain name servers, or DNS
Are Certifications Important for Cyber Security Professionals?
A leading cyber security professional doesn't necessarily need to boast a traditional academic background. Due to this fact, certifications have become an industry-standard marker of knowledge and proficiency, and this has led to the development of many options for those who want to upskill for a promising career in cyber security.
Are you looking for expert instruction at an affordable price? Simplilearn offers several certification-focused courses that are accessible to everyone, regardless of their background. Some of our most popular courses include:
Certified Ethical Hacking (CEH) Certification
Have you ever wanted to learn how to hack into networks but are wary of the prospect of getting into trouble? Our CEH Certification will show you that ethical hacking skills can be an entry point into a meaningful and exciting career path.
CISSP Certification
This course will show you everything you need to know to become a Certified Information Systems Security Professional (CISSP). CISSP Certification is one of the most sought-after credentials in today's cyber security job market. A small investment in this training can have an impact on the trajectory of your career.
Cyber Security Expert
Once you've mastered the fundamentals of information technology and networking, you'll be ready to become a Cyber Security Expert. As an advanced course, it offers experienced professionals an excellent opportunity to expand their cyber toolset, laying out a program for those who are motivated to reach lofty career goals in the cyber security industry.
Why Not Become a Cyber Security Expert?
There is a critical and growing need for qualified cybersecurity professionals today. There is also a shortage of those, which means that there is a giant opportunity to get in on this field. Whether you are just starting out, looking to boost your existing skills and credentials, or change your career because you are looking for a new challenge, checkout Simplilearn's Post Graduate Program in Cyber Security that can help attain your goals.
With top-class industry partnerships, university alliances, and accredited by globally-recognized industry accreditation bodies, you can find what you need with Simplilearn.
Lets started practical



1 Comments:
White hat hackers play a vital role in cybersecurity by identifying and fixing vulnerabilities before malicious hackers can exploit them. With the rise in internet usage and cybercrime, the demand for ethical hackers is increasing. They offer crucial protection across various sectors, making their skills highly valuable and sought after in the evolving digital landscape.
Are you looking to enhance your cybersecurity skills? Check out the Ethical Hacking Training in Bangalore offered by Indian Cyber Security Solutions.
Post a Comment
Subscribe to Post Comments [Atom]
<< Home