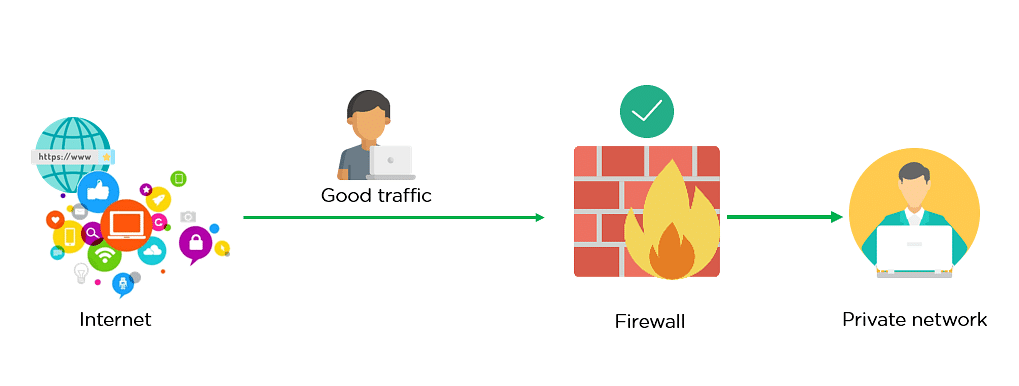
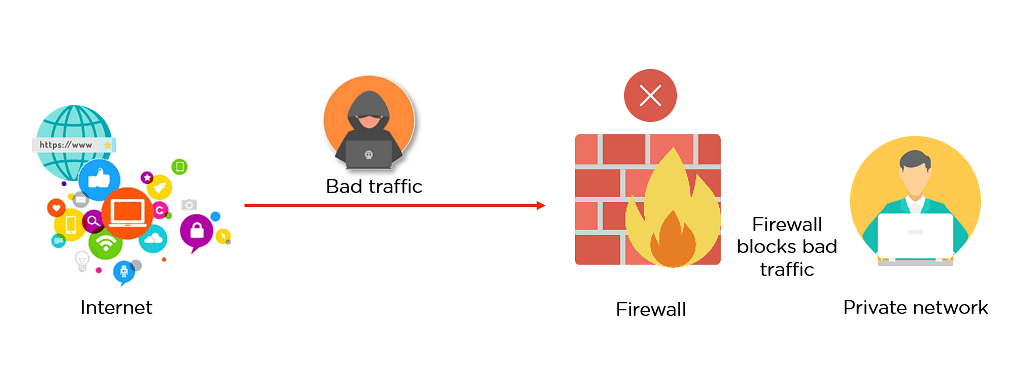
The SHA-256 (Secure Hash Algorithms)
The tenth lesson of hacking :
The SHA-256 (Secure Hash Algorithms)
Among the many advancements seen in network security, encryption and hashing have been the core principles of additional security modules. The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.
To understand the working of the SHA 256 algorithm, you need first to understand hashing and its functional characteristics.
What is Hashing?
Hashing is the process of scrambling raw information to the extent that it cannot reproduce it back to its original form. It takes a piece of information and passes it through a function that performs mathematical operations on the plaintext. This function is called the hash function, and the output is called the hash value/digest.
As seen from the above image, the hash function is responsible for converting the plaintext to its respective hash digest. They are designed to be irreversible, which means your digest should not provide you with the original plaintext by any means necessary. Hash functions also provide the same output value if the input remains unchanged, irrespective of the number of iterations.
There are two primary applications of hashing:
- Password Hashes: In most website servers, it converts user passwords into a hash value before being stored on the server. It compares the hash value re-calculated during login to the one stored in the database for validation.
- Integrity Verification: When it uploads a file to a website, it also shared its hash as a bundle. When a user downloads it, it can recalculate the hash and compare it to establish data integrity.
Now that you understand the working of hash functions, look at the key topic in hand - SHA 256 algorithm.
What is the SHA-256 Algorithm?
SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family, which was slowly losing strength against brute force attacks.
The significance of the 256 in the name stands for the final hash digest value, i.e. irrespective of the size of plaintext/cleartext, the hash value will always be 256 bits.
The other algorithms in the SHA family are more or less similar to SHA 256. Now, look into knowing a little more about their guidelines.
What are the Characteristics of the SHA-256 Algorithm?
Some of the standout features of the SHA algorithm are as follows:
- Message Length: The length of the cleartext should be less than 264 bits. The size needs to be in the comparison area to keep the digest as random as possible.
- Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm, 512 bits in SHA-512, and so on. Bigger digests usually suggest significantly more calculations at the cost of speed and space.
- Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
Now that you got a fair idea about the technical requirements for SHA, you can get into its complete procedure, in the next section.
Steps in SHA-256 Algorithm
You can divide the complete process into five different segments, as mentioned below:
Padding Bits
It adds some extra bits to the message, such that the length is exactly 64 bits short of a multiple of 512. During the addition, the first bit should be one, and the rest of it should be filled with zeroes.
Padding Length
You can add 64 bits of data now to make the final plaintext a multiple of 512. You can calculate these 64 bits of characters by applying the modulus to your original cleartext without the padding.
Initialising the Buffers:
You need to initialize the default values for eight buffers to be used in the rounds as follows:
You also need to store 64 different keys in an array, ranging from K[0] to K[63]. They are initialized as follows:
Courtesy: SHA-2 (Wikipedia)
Compression Functions
The entire message gets broken down into multiple blocks of 512 bits each. It puts each block through 64 rounds of operation, with the output of each block serving as the input for the following block. The entire process is as follows:
Courtesy: Medium Article on SHA 256
While the value of K[i] in all those rounds is pre-initialized, W[i] is another input that is calculated individually for each block, depending on the number of iterations being processed at the moment.
Output
With each iteration, the final output of the block serves as the input for the next block. The entire cycle keeps repeating until you reach the last 512-bit block, and you then consider its output the final hash digest. This digest will be of the length 256-bit, as per the name of this algorithm.
With the SHA 256 algorithm being implemented thoroughly since the early 90s, there are specific applications that you can look into. You will see them in the next section.
Applications of SHA algorithm
As seen in the image above, the SHA algorithm is being used in a lot of places, some of which are as follows:
- Digital Signature Verification: Digital signatures follow asymmetric encryption methodology to verify the authenticity of a document/file. Hash algorithms like SHA 256 go a long way in ensuring the verification of the signature.
- Password Hashing: As discussed above, websites store user passwords in a hashed format for two benefits. It helps foster a sense of privacy, and it lessens the load on the central database since all the digests are of similar size.
- SSL Handshake: The SSL handshake is a crucial segment of the web browsing sessions, and it’s done using SHA functions. It consists of your web browsers and the web servers agreeing on encryption keys and hashing authentication to prepare a secure connection.
- Integrity Checks: As discussed above, verifying file integrity has been using variants like SHA 256 algorithm and the MD5 algorithm. It helps maintain the full value functionality of files and makes sure they were not altered in transit.
How Can Simplilearn Help You?
With hashing and encryption being a staple in today’s digital workspace, it’s no surprise that the demand for has shot through the roof. Apart from cryptography, multiple other avenues in this field are necessary if one wants to pursue a career as a security analyst or network administrator.
Simplilearn offers a course that both newcomers and seasoned corporate professionals can easily pick up. From covering the to teaching its most nuanced characteristics, the course is filled with tasks, live classes, and a solid foundation to start your career in this lucrative field.
Conclusion
In today’s lesson on SHA 256 algorithm, you learned the basics of hashing, the applications of hashing, the origin of SHA, its working, and the places this algorithm finds use. Hopefully, this has been an exciting session for you.
Do you have any questions regarding any part of this tutorial? Please let us know your thoughts and questions in the comment section below, and we will have our experts look at it for you.